There is a lot of hype surrounding security tokens these days, especially as the SEC has almost entirely suffocated the usage of utility tokens as unregistered securities. Security tokens are evolving as a new strain of cryptographic tokens, that are not only fully compliant with the SEC’s regulations, but also backed by real-world assets.
Even though the security token market is evolving at a rather fast pace, the industry is still in its very early days. As such, there are numerous grey areas lying in both the market presented to token buyers, as well as the business models adopted by entrepreneurs and business owners looking to raise capital via regulated blockchain-based means.
Throughout this guide, we will walk you through and explain some of the basic concepts and definitions related to security tokens and security token offerings (STOs).
What are security tokens?
What does security token mean? Quite simply, security tokens are cryptographic blockchain based tokens that represent financial assets such as bonds, notes, debentures, shares (stock), options, and warrants. Holding security tokens representing company shares is a way to own a part of a company, without actually taking possession of it.
Governmental financial institutions and companies can utilize security tokens to raise money for various investors via security token offering (STO) based crowd sales. STO investors are promised gains in the form of dividends, staking rewards (interest rates), or increase in the value of the company.
Security tokens have minimal liquidity issues when compared to conventional securities (paper backed securities such as bonds, stocks, futures, etc). With security tokens, investors’ dividends can be paid on a predefined date in the form of tokens via a specifically designed smart contract.
Another security token definition is that security tokens have to pass “Howey’s Test”, which was developed by the Supreme Court for determining if a transaction qualifies to be considered a form of “investment contract”. As per the Securities Act of 1933, as well as the Securities Exchange Act of 1934, cryptographic tokens passing the Howey Test will be considered security tokens, rather than utility tokens. As such, security tokens are subjected to specific registration and disclosure requirements.
The Howey Test considers a cryptographic token to be a security token if it involves:
1- Investment of money
2- A common enterprise
3- Profit expectations
4- Work efforts of others
Observers of the cryptocurrency market can mark the occurrence of three waves of security tokens:
- The first wave of security tokens: Security tokens exempted from the US SEC regulations. Security tokens from this category utilize regulatory exemptions for reputable, wealthy investors. These tokens have been used by cross-border investors. This wave of security tokens began in 2017.
- The second wave of security tokens: Security tokens that will revolutionize identity management to yield a wave of security tokens that are compliant with US SEC regulations. Anti-Money Laundering (AML) and Know Your Customer (KYC) regulations are automated via a new technology that sits on top of the blockchain layer of smart contracts. Hashing of AML and KYC regulations on a country-by-country basis can render cross-border transactions more feasible and more efficient. This wave of security tokens started in 2018.
- The third wave of security tokens: This wave of security tokens is pillared on the reduction of regulatory risks, and seeking more innovative financial opportunities. These security tokens will focus on improving liquidity, boosting cross-border trading liquidity premiums, promoting compliance with AML and KYC regulations, and reducing settlement times. The third wave has the potential to properly tokenize existing assets, and automate the management of dividends, as well as STO team token lock-ups (vesting). In 2018, security token trading emerged, yet this required security token trading organizations such as Security Token Alternative Trading Systems (ATS), which represent hybrid platforms that can be used for both the issuance and trading of security tokens.
How do security tokens work?
Security tokens work to raise money for a startup, or a company. Actually, as a way of raising capital for startups, or established companies, the STO represents a logical extension of the concept behind ICOs and IPOs. In the United States alone, more than 650,000 companies are established each and every year. Wall Street, Silicon Valley, and venture capitalists do not provide sufficient capital for all these new companies. As such, regulated and legally compliant security token offerings (STOs) are providing a new source for the needed funding. Even though approximately $5.6 billion was raised globally via ICOs and STOs in 2017, more than $36 billion was raised via IPOs in the US alone in the same year. It’s clear that ICOs and STOs aren’t poised to replace the IPO, but they can serve as a viable alternative for many companies.
Security tokens can also work to help in the tokenization or securitization of existing real-world assets. The process of tokenization, which is also known as crypto-fractionalization, of global real-world assets represents another potential opportunity for security tokens. The world’s equity assets value around $70 trillion, and real estate assets are estimated to exceed $230 trillion ($180 trillion in residential properties, $32 trillion in commercial properties, and the remainder in agricultural real estate). All these equities represent seeds for security tokens, formulating a market that has just begun to emerge in 2018.
Mass adoption of security tokens will replace much of the current paper work used in trading of securities. Security tokens will minimize the overall cost of administration of today’s financial systems. It is estimated that the world can save up to $6 billion each year, spent on paper-based financial systems, if security tokens are massively adopted across equity markets.
What do security tokens do?
In all the conversations around security tokens, it can be difficult to determine what security tokens actually do, and what is just speculation. Additionally, it’s important to be aware of what qualities are unique to security tokens, and what facilities were already available but are simply made easier or more efficient through the addition of blockchain technology.
For instance, it was already possible to fractionalize real-world assets, most commonly in the form of shared real estate investments. What tokenizing these assets does is make it quicker and easier to transfer ownership of these fractionalized assets, as well as reducing the expenses associated with such a transfer.
Likewise, Regulation S already gave companies access to foreign investments. Security tokens simply serve as a method to use Regulation S for token sales.
Security tokens are seen as democratizing the fundraising process, but in truth they are less democratic than ICOs and other forms of crowdfunding. Due to the unfortunate abuses of the ICO system, many are now forced to turn to STOs instead, which leaves out those investors who may not be able to meet the requirements of becoming an accredited investor in an STO.
And what of cost? While some have speculated that it will eventually be more affordable than traditional forms of launching securities, it is actually currently more expensive. Most experts believe that the prices will eventually even out, and that it is unlikely we’ll actually see security token issuance become the more affordable option. And to be sure, an STO is more expensive to launch than an ICO, but for some projects, they may have no choice in the matter if they wish to be in compliance with the regulations of their jurisdiction.
What then are the true benefits of security tokens and STOs?
Mainly, the benefits lie in the speed, efficiency, and technological advancements associated with blockchain technology.
Securities laws are complicated and convoluted, and can vary widely from jurisdiction to jurisdiction. This leads to a compliance nightmare for those looking to transfer their securities. Blockchain-enabled smart contracts, however, can have the securities rules hardcoded into them, so that they can only be traded when compliance is met. This will provide companies and investors with powerful protection against securities fraud. Even complicated cross-border transactions will be much easier thanks to the blockchain.
The frictionless nature of security tokens should also increase the existing liquidity of the market. When it is faster, easier, and more affordable to exchange securities (in whatever form they take), this should lead to more movement in the market.
The blockchain also brings a new level of transparency to securities, making government oversight easier. This may not hold much appeal for those crypto purists who prefer decentralized currencies with no government involvement, but for those who are in the mass adoption camp, anything that gets governments onboard can only be seen as smoothing the way for greater acceptance and utilization of cryptocurrency.
In essence, what security tokens aim to do is bring the benefits of the blockchain to the traditional securities space. Frictionless transactions, transparency, smart contracts, and other aspects of blockchain technology should improve this existing market.
What is a security token platform?
Many of the current cryptocurrency exchanges don’t perform the required due diligence on their users to identify who can and cannot invest in certain security tokens. With decentralized crypto exchanges, the problem is even more complex.
Alternative trading systems (ATS), or security token platforms, are regulated crypto platforms specifically established for issuance of security tokens. These platforms aim to solve liquidity problems which are by far one of the main obstacles hindering mass adoption of security tokens. Liquidity represents the ease and stability via which a security token can be purchased and sold on the market. Currently, the security token market is marked by extremely low levels of liquidity, due to the low number of operating, regulated security token exchanges.
Security token platforms simplify the process of issuance of security tokens. These platforms will not only issue a security token for you, but will also help you go through all the needed paperwork and legal procedures to be fully compliant with the SEC’s regulations, or the securities’ regulations of the country jurisdiction where you choose to issue your token. Security token platforms will help you pick the right KYC/AML provider for your STO.
The security token platforms available currently include Polymath, tZero, Swarm, Harbor, Securrency, and Securitize.
Polymath
Polymath is working to become the “Ethereum for security tokens”. Polymath has developed the ST-20 token standard on top of Ethereum’s blockchain. The platform provides all the required legal and technical solutions to tokenize stock, bonds, or any other asset form on the blockchain.
Polymath has issued its own native token, POLY, to be used as a currency for all economic operations taking place on Polymath’s platform.
Polymath is considered a leader in the security token exchange market sector, and has established a partnership with tZero, a security token exchange which will promote the liquidity of security tokens issued on Polymath’s blockchain.
Harbor
Harbor is a blockchain based trading platform specifically established to issue security tokens and help them through the process of compliance with the current regulatory framework. Harbor also helps existing companies tokenize their assets and shift to blockchain based shares. Harbor utilizes a regulated token system that relies on R-Token.
R-Token is an Ethereum based permission token which enables token transfers to take place only if they get approved by an on-chain Regulator Service, which is set up to be fully compliant with the SEC’s regulations.
Securitize
Securitize is a blockchain based trading platform that serves as an end-to-end platform for issuance of tokens for the tokenization of real-world assets. These assets can be in the form of a company, a fund, a real estate property, or any other form of real-world assets.
Securitize is designed to manage the processing of solicited investors, from login authentication to capital receiving, in addition to the issuance and management of security tokens all through the lifetime of the tokenized asset.
Securitize accomplishes this via their unique DS protocol that operates via its DS tokens. DS tokens are Ethereum based ERC20 tokens that deploy the additional hooks required by the DS protocol.
Swarm
Swarm is a blockchain based platform for the tokenization of real-world assets. Swarm relies on the SRC20 protocol, which is a cryptographic standard especially formulated to tokenize assets. Assets that can be tokenized through Swarm can include companies, real estates, agricultural projects, renewables, cryptocurrency hedge funds, and more. The platforms facilitates the governance, management, and trading of tokenized real-world assets.
The SRC20 protocol prescribes a definitive set of rules which must be incorporated in security tokens to represent the tokenized asset. This standardization helps programmers to develop applications that can use these security tokens. SRC20 based security tokens can perform the following:
– Represent ownership of a part of a tokenized asset
– Enable token holders to manage tokenized assets via voting
– Secure rights to assets’ revenue streams
– Provide a regulatory compliant ecosystem for trading of security tokens
The platform’s native token is SWM, which facilitates economic operations on the Swarm platform.
Securrency
Securrency is a platform for the tokenization of real-world assets and issuance of security tokens. The platform features a simple “drag and drop” procedure for the issuance of security tokens via a few clicks. The platform also boasts a unique engine, known as RegTex, that conducts KYC for customers from 160 countries, in addition to AML for fiat and cryptocurrency wallets. RegTex also verifies the sources of funds and accredited investors.
Additionally, Securrency offers users special APIs and abstraction layers known as Securrency’s flexible InfiniXChange to pick a blockchain of their choice.
tZero
tZero is a security token exchange that is partnering with the market leader Polymath. The blockchain based technologies offered via tZero are aimed at revolutionizing the security token market, as well as fixing the inherent inefficiencies of Wall Street. tZero is designed to render financial operations less beholden to conventional, institutional market frameworks.
The platform also has its native token, the tZero token, which fuels all trading operations conducted on the platform.
Buying security tokens via an STO or exchange
If you are wondering how to buy security tokens, they can be bought via a Security Token Offering (STO), or via a security token exchange, which is occasionally referred to as Security Token Alternative Trading Systems (ATS).
Purchasing via a Security Token Offering (STO)
Participating in a STO is similar to participating in utility token ICOs. You can buy tokens during an STO from the project’s website. You can then hold, sell, or trade your purchased tokens. Due to the fact that security tokens represent financial securities, your purchased tokens are backed by tangible holdings such as assets, the company’s revenue, or profits.
STOs are launched on ATS based platforms such as Polymath, Swarm, Harbor, or others. Before issuance, companies launching an STO will be guided through a set of technological and legal processes. Security tokens issued this way are compliant with the requirements of KYC and AML, as well as the securities laws in the particular jurisdictions they touch. Security tokens launched using Polymath’s ST-20 standard can prevent trading between individuals from excluded countries via means of smart contracts and the platform’s whitelisting technology. As long as you meet the requirements, it is easy to figure out how to invest in security tokens.
Security Token Advanced Trading Systems (ATS)/Security Token Exchanges
You can buy security tokens via one of the following security token exchanges presently available on the market:
tZero
tZero is not only a security token exchange, but also a security token issuance platform. The exchange is extremely simple to use. Its partnership with Polymath simplifies the legal verification process that users have to go through before actually trading security tokens. tZero features a smart order matching engine and a risk management system, which are fully compliant with security token trading. On tZero, users can trade tokens based on the ST20 standard, which is a unique Ethereum standard innovated by Polymath. The ST20 standard tokens can only be bought by Ethereum addresses whose owners have completed KYC verification procedures.
BankToTheFuture (BTF)
BankToTheFuture (BTF) is a security token investment platform/exchange which can only be accessed and used by professional investors. The platform is only open to investors with a yearly income of at least $200,000, who can commit to investing at least $1,000 with BTF yearly.
Bancor
Bancor is a security token exchange that has developed its very own Smart Token protocol, which is considered a precursor for the emerging era of decentralized cryptocurrency exchanges. Security tokens based on the Smart Token protocol are automatically convertible to other tokens on Bancor’s network via a unique technology that operates similarly to Atomic Swaps.
Bancor has its own native token, the BNT token, which acts as a bridge token that can intermediate the exchange process between any pair of security tokens featured on the exchange.
Security token offering process
Let us take you through the process of setting up a security token offering (STO).
Understanding regulations and legal compliance
Before launching a security token offering (STO), you have to understand the federal security regulations, especially if you are looking to accept investors from the USA. In the US, security tokens have to be compliant with one of the following regulations:
– Regulation D
– Regulation A+
– Regulation S
Regulation D
Regulation D will allow an STO to avoid registration with the SEC, provided that the issuers of the tokens have filled “Form D”, after the security tokens have been sold. The party who is offering the security tokens can solicit offerings from investors in compliance with Section 506C.
Section 506C requires a verification implying that investors are provably accredited and that the information provided throughout solicitations is “free from misleading or false statements”.
Regulation A+
This exemption will enable the creator of the STO to offer an SEC-approved security token to non-accredited investors via a general solicitation for an investment totaling up to $50 million.
For the requirement to successfully register a security token, the issuance of Regulation A+ can consume more time when compared to other options. For the same reason, issuance of Regulation A+ is considerably more expensive compared to other options.
Regulation S
This occurs when an STO is launched in a country other than the US, and is thus, not subjected to the registration requirements of section 5 of the 1993 Act. The creators of the STO still have to comply with the security regulations of the country where the STO is supposed to be launched.
When to launch an STO?
We recommend launching an STO to raise capital for a company or start-up which meets 2 or more of the following criteria. As such, consider launching an STO if your company is:
– Expected to generate at least $10m of revenue annually
– Planned to be a high growth start-up
– Conducting cross-border business
– Designed to issue transferable shares of an asset
– Interested in means of funding that connect with the company’s customer base
– Looking for higher levels of liquidity for holders of shares of the company
Identifying your target customer base
Creators of STOs can look for full registration with the SEC, which is a legal, financial, and logistical dilemma. To skip this step, the company has to go for an “SEC exemption”. To accomplish this, you have to go for Regulation D exemption, which prohibits sales to non-accredited investors from the US.
On the other hand, you can go for Regulation A exemption. Securities group Tripoint Global is on its way to become the first ever regulated company to offer sales of security tokens under SEC’s Regulation A, i.e. it can sell security tokens to non-accredited investors from the US.
However, currently, you can only sell security tokens to accredited and non-US investors. Accredited investors refer to either individuals or institutions with a net worth of at least $1 million. You should only target these two groups in your STO marketing.
Best country jurisdictions to launch your STO
Legal issues represent the most significant hurdle facing the STO model worldwide. Even though it is currently illegal to raise capital via STOs in most country jurisdictions, a few others have established very friendly legal environments for the STO fundraising model. Currently, the best country jurisdictions to launch your STO include Malta, Canada, Estonia, Switzerland, Germany, and Lithuania.
Malta
Malta is inarguably the best country to go to in order launch your STO, especially considering that the country’s officials have repeatedly expressed their willingness to turn Malta into an international hub for STOs. The country has decided to establish a legal framework for STOs, which is based on three acts that had been unanimously passed by the Maltese Parliament:
1- Malta Digital Innovation Authority Act (MDIA)
The MDIA act provided legal, tokenomic, and technical definitions to users on blockchain based platforms in Malta. It also guaranteed that blockchain technology service providers can operate in a legal and transparent atmosphere.
2- Innovative Technological Arrangement and Services (ITAS) Act
The ITAS Act details the guidelines for certifying and auditing software and frameworks aimed at establishing blockchain-based startups, DAOs, smart contracts, and cryptocurrency exchanges.
3- Virtual Financial Asset (VFA) Act
The VFA Act established a framework for regulations that can be applied to individuals and businesses dealing with virtual financial assets such as ICOs, STOs, cryptocurrency exchanges, cryptocurrency wallet providers, portfolio managers, brokerages, and investment advisors. As dictated by the VFA Act, issuers of cryptographic tokens (ICOs and STOs) have to appoint a VFA agent for monitoring and reporting on the process of token offering.
These three acts show that Malta has developed a novel legal framework for STOs, rather than trying to force them to comply with existing regulations. This can explain why Malta is the world’s most friendly jurisdiction for launching an STO. Other country jurisdictions, e.g. USA, are attempting to regulate STOs via modifying their existing stock market and IPO laws. These jurisdictions usually just examine white papers to extract concept ideas, enforce AML/KYC regulations, and formulate laws that are merely based on the type of token sold via ICOs or STOs.
Canada
Canada is a very STO-friendly legal jurisdiction, provided that the token sale is launched according to the guidelines described in the regulatory ICO/STO sandbox released by the Canadian Securities Administrators (CSA). A group of strict guidelines were set by the CSA for issuance of prospectuses and offerings memorandums (OM) prior to launching as STO. The OM has to include clear information regarding the project’s roadmap, identities of the team of founders, and the potential risks associated with investing.
As entailed by the CSA, entities involved in an STO have to complete a dealer registration prior to launching the token sale. Moreover, companies qualifying for the business trigger have to meet a group of financial obligations to investors, namely KYC details and other relevant suitability requirements.
Switzerland
Switzerland is also one of the world’s best jurisdictions to launch an STO. STOs are regulated by the Swiss Financial Market Supervisory Authority (FINMA), which treats security tokens similarly to conventional securities such as stocks, futures, and bonds. As such, any company offering an STO has to comply with the same laws regulating securities. Within the same vein, STOs have to comply with KYC regulations, in order to prevent various forms of fraud.
Moreover, STOs are also subjected to the Swiss “Big Five” Banking Regulations – The Anti-Money Laundering Regulations, the Stock Exchange Act, Financial Market Infrastructure Regulations, Banking Regulations, and Collective Investment Scheme Regulations. These regulations are formulated to promote a fair and ethical market environment and to protect investors.
Observers believe that Switzerland is likely to evolve into a hub for tokenized securities during the next few years, especially given that country already boasts a promising track record with a large number of cryptocurrency projects.
Estonia
Estonia is following in Malta’s footsteps via establishing a friendly legal environment for security tokens. The Estonian Financial Supervision Authority (EFSA) treats security tokens as traditional securities, according to the legal definition introduced via the Securities Market Act (SMA) and the Law of Obligations Act (LOA).
All STOs should be supervised by the EFSA, which requires the issuer of an STO to present a prospectus including all the information included in the Prospectus Regulation (Regulation (EU) 2017/1129). The most important required information include the following:
– Registration document that includes detailed information on the security token issuer
– Security note that includes information about the nature of the security token
– Description of risks associated with investment in the project
– Details of how raised funds will be used
Germany
Germany has decided to adopt a friendly legal attitude towards cryptocurrency-based projects in general, which urged Bitbond, the P2P cryptocurrency lending platform, to launch its STO there, to become the first ever STO to be launched in Germany.
The issuer of a security token must draft a prospectus prior to launching the STO, in order to obtain a license from BaFin, which is Germany’s securities regulation authority. Moreover, STOs have to comply with other German regulations including the German Securities Trading Act (WpHG), the European Market Abuse Regulation (MAR), and the European Markets in Financial Instruments Regulation (MiFIR).
Lithuania
Lithuania is one of the most STO friendly European countries, as the country’s officials have repeatedly expressed their intentions to turn Lithuania into a security token hub, especially considering that the country is already one of the world’s most prominent Fintech hubs, thanks to its extremely friendly blockchain initiatives. Lithuania is compared to Malta, which is recognized as the world’s top blockchain hub, hosting hundreds of ICOs and cryptocurrency based firms.
DESICO is a blockchain based platform offering the full spectrum of security token related services, which is endorsed by the Lithuanian Ministry of Economy and Ministry of Finance. Moreover, Lithuania is one of a handful of countries all over the world that have a special legal framework regulating retail investment in the STO industry. As such, Lithuania can be considered one of Europe’s best country jurisdictions to launch an STO.
Issuance of your security token
One of the biggest problems associated with security tokens is liquidity. Prior to advent of the blockchain, trading fractional ownership of assets with low liquidity levels, such as private equity funds, or real estate investments, was almost impossible. With blockchain-based asset tokenization, the problem is much less prominent.
However, there are a few catches. Tokens have to remain legally compliant as they change hands, which mandates ongoing implementation of KYC/AML regulations all through the lifecycle of the token. Security token buyers must have a legally compliant platform to find one another: a security token exchange. The SEC has decreed that all crypto exchanges which list security tokens should register themselves as securities brokers.
Consequently, you have to pick one of the registered security issuance platforms to launch your STO. These include one of the security token platforms that we mentioned earlier such as Polymath, Harbor, Securitize, and others. As an example, we will walk you through the process of creating a security token via Polymath.
(Note: in the screenshots illustrating the following steps, we redacted the ethereum address and transactions of fees paid for our demo token. Apart from this, the screenshots reflect exactly what you would encounter when creating your security token using Polymath’s security token issuance service).
1- Fund your Ethereum Metamask wallet:
You have to have ether funds on your Metamask wallet, before you can start issuing your very own security token. Metamask is an Ethereum wallet that you can access via your own internet browser. If you don’t already have a Metamask wallet, you can download the Metamask Chrome extension, via this link. Then, fund your wallet with some ether.
Next, point your browser to https://polymath-issuer.netlify.com/ and then click on the “Create Your Security Token” button to start the process, as shown on the below screenshot.

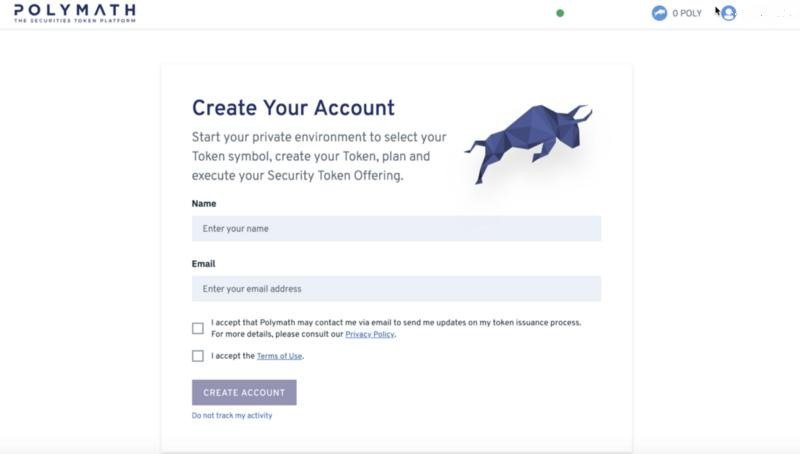
2- Create your account:
To proceed with the process of creating your account, you will have to sign in to your Metamask wallet by clicking the Metamask icon on the top bar of your Chrome browser, and entering your password or mnemonic passphrase. By doing this, you will link your Metamask wallet to your Polymath wallet after creating your account.
Now, create your account on Polymath’s platform by entering your name and email address. Then, accept Polymath’s privacy policy, as well as its terms of use, and click “Create Account”, as shown on the below screenshot.
3- Reserve your token symbol: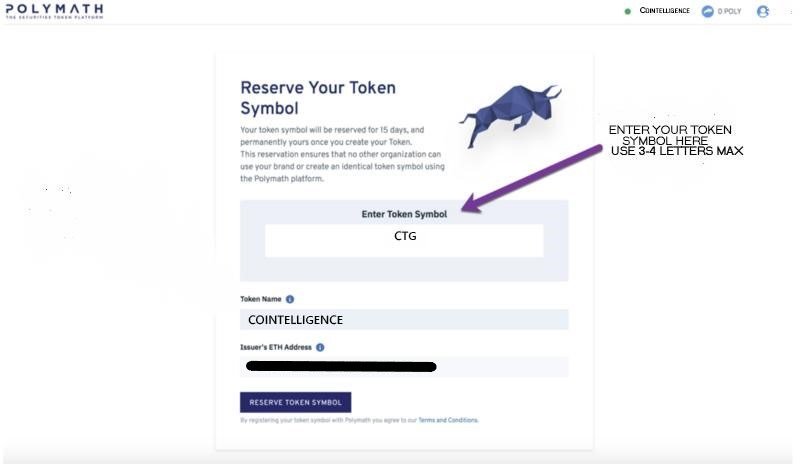
Next, pick your token name and symbol and click on the “Reserve Token Symbol” button. This step will enable you to reserve a token symbol, so that no one else can use it. As shown on the above screenshot, we named our token “Cointelligence” and picked the “CTG” symbol for it.
After choosing your token name and symbol, you will be given a 15 day period to consult with your lawyers and advisors. You will be prompted with a pop-up window asking you if you are satisfied with your choices. If everything is OK, click the “Reserve Ticker” button, as shown on the below screenshot.
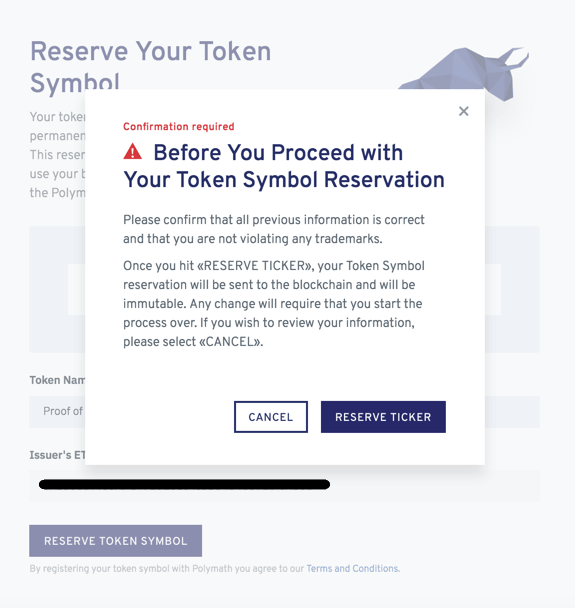
After submitting your token symbol reservation request, the platform will automatically send information about your security token offering to the email address you used to create your Polymath account. You will have to verify your email address to be able to receive this information.
After confirming your email address, you will receive an email that includes a link to the transaction of the payment for registration of your STO.
4- Pick your providers:
In this step, you will get to select the partners who will help you throughout your STO campaign. You will have the opportunity to build your team via picking the right AML/KYC providers, marketing team, and legal advisors.
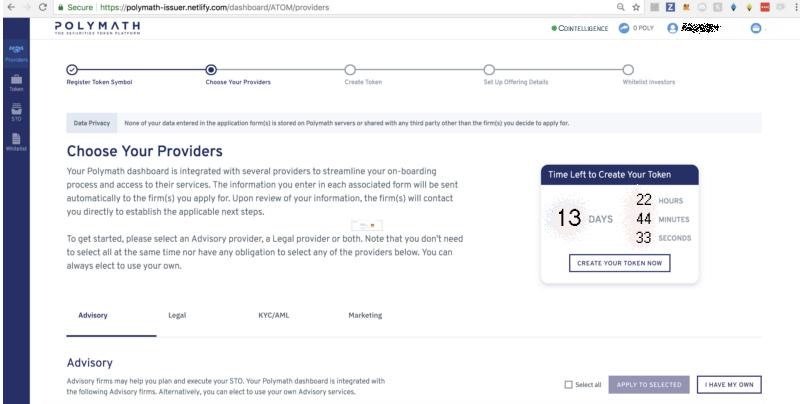
Even though the platform will not send you emails to notify you regarding the service providers you selected while still running on testnet, you will be sent a sample email copy that would otherwise be sent to them.
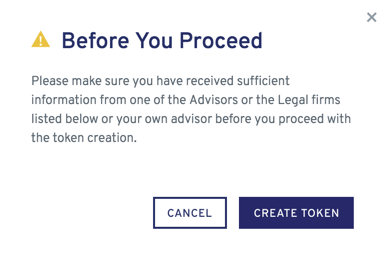
Now, click on the button marked “Create Your Token Now”. You will be prompted with a pop-up window asking you to make sure that you have received sufficient information from one of the listed advisors or legal firms before proceeding.
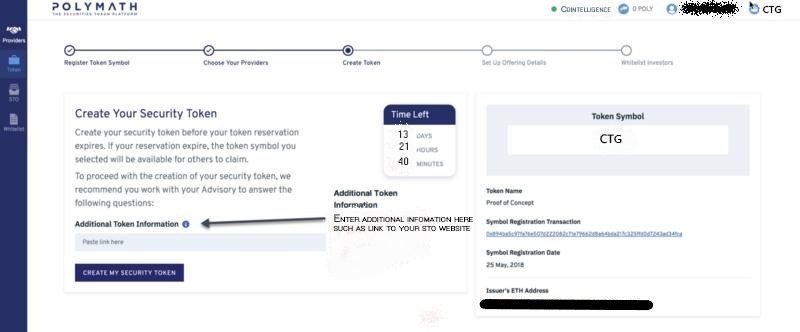
5- Create your own security token:
Now, you can enter any additional information such as a link to your STO website in the blank box provided, as illustrated on the below screenshot.
Afterwards, you will have to click “Submit” on the Metamask wallet browser extension to signal issuance of your security token. A copy of the ethereum transaction hash will be sent to your email address.
6- Set up the details of your STO:
The final step of the process is clicking on the button marked “Set Up Your Offering Details”. When doing so, you will be prompted with a screen like the one shown in the below screenshot.
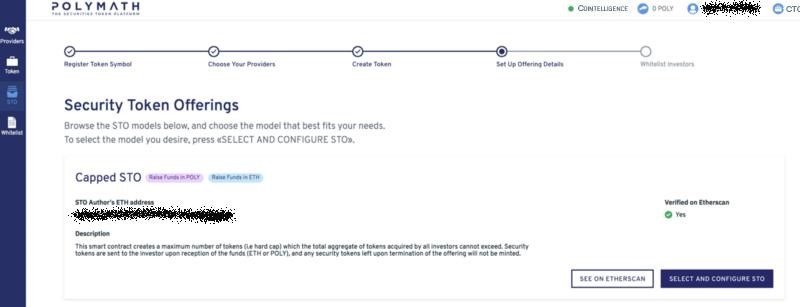
When selecting a capped STO, you will offer a predetermined number of tokens for sale at a specific price per token. After the token ceiling amount is reached, no more tokens can be sold. After going through this step, finalize your STO’s details via clicking the “Select and configure STO”, as shown on the above screenshot.
This step should also include other details for your security token offering, such as:
– The start and end date of your token offering;
– Currency accepted (ETH, POLY, or both)
– The rate at which the tokens will be valuated
After filling in all the required details, click on the “Confirm and Launch STO”. By doing so, you will be prompted with a page like the one shown in the below screenshot.

7- Whitelist the STO’s investors:
This is the final step in the process of setting up your STO. You will have to create a whitelist for the investors who will be able to buy tokens during the STO. Your created whitelist will determine the countries allowed to participate in your STO. You will rely on your legal team and advisors to create your whitelist. Note that you can update your whitelist before, during, or even after the end of the STO. When you whitelist investors, you will see them included in the whitelist table as shown on the below screenshot.

This has been a summary of the steps that you will have to go through to create your security token via Polymath. From here, your next steps could be to promote your new STO via social media and inclusion on a security token offering (STO) list.
Final thoughts
The cryptocurrency community has been extremely relieved that the SEC decided not to consider cryptocurrencies, namely bitcoin and ethereum, as securities, due to the fact that they have been categorized as utility tokens. Currently, security tokens represent an extremely low market share when compared to utility tokens, and it’s still common to hear questions like “What is a security token service?” and “Isn’t STO just another name for ICO?”. Nevertheless, observers predict the security token market to exhibit a logarithmic rate of growth during 2019. Billions of USD worth of capital is expected to flow from Wall Street and Silicon Valley into security tokens, rather than utility tokens, during the upcoming couple of years. This shift from ICOs to STOs is happening simply due to the fact that with legal compliance, more investors are expected to pour in, and bigger capitals are to be invested in security token based business models.
Security tokens are expected to entirely change the equity market, the same way bitcoin changed currency. This is because security tokens offer investors not only liquid economic interests, but also expedited proceeds’ delivery. We are in a brand new era where every form of asset ownership can be tokenized – it is a market that can be worth more than multi-trillion USD in the next few years.

