Not your keys, not your crypto
‘How do I store my…?’, is one of the most asked questions in the cryptosphere. One that is posed by newcomers, veteran traders, institutions and everyone in between — an important question too. As high-profile attacks, hacks, and negligence become more prevalent with crypto exchanges, custody risk should be a concern for every type of crypto holder.
In this article we will discuss how private keys and crypto storage works, which options you have available and share some crypto storage tips and best practice.
How private keys work
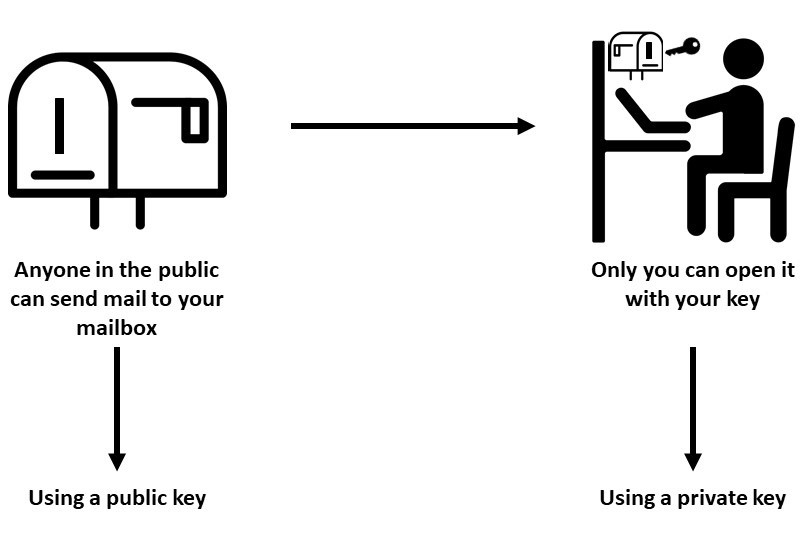
A cryptocurrency wallet is a bit like a digital mailbox. A mailbox has an address, for example:
Postbox 012008
Satoshi’s Place
Any member of the public who knows this address can send you mail. However, if this is your mailbox, then only you should hold the key which can open that mailbox and collect that mail.
The same is true with public and private key cryptography on which cryptocurrency is based. When you create a cryptocurrency wallet you will be presented with a public key or ‘Address’ which is used to receive cryptocurrency. You will also be presented with a private key which you must store responsibly as you would your mailbox key.
A private key may look like this:
3a1076bf45ab87712ad64ccb3b10217737f7faacbf2872e88fdd9a537d8fe266
A public key may look like this
0xC2D7CF95645D33006175B78989035C7c9061d3F9
The private key is unique and acts like a digital signature which makes it far more useful than a physical key, like signing smart contracts. Unlike a mailbox, a cryptocurrency wallet will only ever have one private key but can have many public addresses associated with it.
Different storage solutions
There are many options for key storage, all of which vary in their complexity, cost, and level of security.
How to store your crypto will largely depend on the type of crypto in question and the value which is held, but there is always one golden rule — YOU must be in control of it. This means that YOU maintain ownership of your private keys and only YOU will have access to the assets held therein.
The main objective of storing your own private key is to have some degree of separation between your private key and your extremely vulnerable, internet connected devices such your laptop or smartphone.
Physical backup
For users which are holding smaller amounts of crypto, you might need lower levels of security and might be suited to storing an encrypted backup of your private key in one or two physical locations to protect against the loss of a device or forgetting your key. This can be done by writing down your private key on a piece of paper or storing it on an encrypted flash drive. You can make use of non-custodial wallet services to access your assets when needed. Examples are, MyEtherWallet, Metamask or others depending on your needs.
Hardware devices
Hardware wallets are typically the best at balancing the ease of use and high level of security. A hardware wallet works similarly to a two-factor authentication device you may use with your bank. These devices allow you to store private keys offline in a physical, password protected device while also being protected from malware and hackers coming from internet connected devices. These may set you back anywhere from $50 to $500. Popular wallets include Ledger and Trezor.
Advanced security
If you are holding large amounts of crypto you will need to meet the aforementioned but also have advanced security controls to protect your assets from instances of seizure or even targeted attack.
Typically, advanced security should require some type of multi-person consensus to be accessed. This may include private key fragmentation or the use of multi-signature addresses.
It is recommended to never store your private key with a custodial service like a centralized/legacy exchange, or even supposed ‘high security’ online storage solutions.
Remember: if you don’t own the key, you don’t own the assets.
Store safe, trade safe
The risk of legacy/centralized exchanges
Most crypto exchanges act as custodians of your assets. This means that when you use these types of exchanges you are effectively giving up ownership of your private key while your assets are held at the exchange. This exposes you to counterparty or custodial risk. In the event the exchange or ‘custodian’ is attacked or falls victim to employee misconduct, you may lose or be prevented from withdrawing your assets from the exchange. Granted, many exchanges have dedicated security teams to fight this battle for them but as the adage goes, security specialists need to win every battle, a hacker only needs to win one.
The rise of non-custodial trading
Non-custodial exchanges, like Counter, allow users to trade without giving up custody of their private key — therefore reducing the impact of counterparty or custodian risk to near-zero. This type of trading mechanism has been implemented by a number of exchanges in various ways. Counter achieves this by replacing centralized wallets with decentralized smart contracts. All smart contracts require a digital signature from the user to execute (signed using their browser-enabled wallet), meaning only you (the private key owner) can move, withdraw or trade the asset.
In Conclusion
In this digital era of crypto we have been given the ability to take back control of what is ours. With this power comes great responsibility — by not taking the appropriate measures to protect one’s private keys, your funds are no more secure than leaving your cash at the end of a table. However, with just a small amount of effort you can secure your crypto far better than any legacy financial institution might charge you for doing. It is recommended to never store your keys using an exchange. Instead, keep your private keys private, access your assets as and when needed through non-custodial platforms like MyEtherWallet and trade assets through non-custodial exchanges like Counter.
Disclaimer: The author is the co-founder of Counter.
Author image: