On the 3rd of June, ZenCash suffered from a 51% attack where more than $500,000 in double spend transactions was lost. The attacker managed to manipulate blocks which allowed him to double spend on two massive transactions of respectively 13,000 and 6,600 ZEN. According to estimates via the website 51Crypto.app, the attacker only had to spend $30,000 to pull off the 51% attack.
TLDR; A 51% attack refers to a double-spend attack on a blockchain where an entity or group of persons controls more than 50% of the network’s mining hashrate. This gives the attackers massive control over the network and the transactions happening on it. It basically means they can manipulate transactions, revert them, or change the destination, enabling them to spend them twice.
ZenCash is not the only victim of recent a 51% attack - MonaCoin, Bitcoin Gold, Verge, and Litecoin have been attacked as well recently. It’s clear that the cost of a 51% attack isn’t that high for many smaller - and less popular among miners - Proof of Work (PoW) coins. This article discusses the following topics:
Crypto51.app is a website that wants to bring awareness among smaller cryptocurrencies to show them how easy it is to complete a 51% attack on their network. The cost is calculated using NiceHash prices, a website that offers hashrate (mining) power on various cryptocurrencies as a service. The price is based on matching the hashrate of a specific Proof of Work network for one hour. The price does not include the block rewards the attacker may receive, according to Crypto51.app, “this can be quite significant, and reduce the attack cost by up to 80%.”
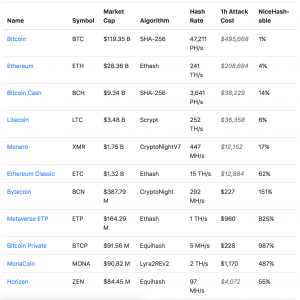
Shockingly, several smaller cryptocurrencies have plenty of hashrate for sale on NiceHash, making themselves vulnerable for a 51% attack. In the introduction we mentioned MonaCoin; Crypto51 shows us that they have almost 5 times the amount of hashing power needed to perform a 51% attack for sale via NiceHash. Here’s an extract of the list, mind Bitcoin Private and Bytecoin.
Robert Viglione, co-founder of Horizen, puts Crypto51.app into perspective, ”Proof of Work is the most battle-tested consensus mechanism and so it’s something we shouldn’t abandon lightly. Hijacking networks is now too easy, though still much more difficult than sites like crypto51.app present.”
“One still needs to buy a large amount of the target coin—these funds are at risk as the attacker is performing actions that directly undermine its value—and then gamble real money on stochastic outcomes. It involves good timing, luck, and nontrivial resources to pull off.”
Would performing a successful double spend be considered illegal?
It’s a tough discussion about whether a successful double-spend is considered illegal. On the one hand, you are stealing money as people won’t receive the funds they should have received. On the other hand, there’s not really a law that recognizes international alternative currencies. Bitcoin and most other cryptocurrencies have no terms and conditions that promise to give you something in return for the currency, and no central authority to form an agreement with.
According to Chris on StackExchange, “A double-spend would be blackletter law illegal as fraud and theft include a wide variety of intentional deception wrongfully depriving someone of property - use of a government-minted currency is not, and never was a required element. Look at any larceny or fraud statute - it will refer to loss of or damage to a person and property, not monetary dollars."
If you are in the US, the law is very broad. The Computer Fraud and Abuse Act (18 U.S.C 1030) protects companies and persons against any digital attack or theft, and so, can be applied to almost any digital crime.
Should new projects use other mining algorithms as they put themselves at risk using PoW?
PoW is challenging for a new project that doesn’t start immediately with strong mining support. However, what’s also true is that the economic incentives to attack small networks just aren’t there. Why risk real funds for no reward? This is why small networks rarely get attacked. Proof of Stake (PoS) and other consensus variants have also proven to be promising thus far, so new projects ought to consider them, but there are always tradeoffs.
For sure, these marketplaces which rent mining power as a service add a centralizing element to what were intended to be more decentralized mining environments. Robert Viglione thinks we just need to be more creative on the entrepreneurial side to continue decentralizing when and where it makes sense.
Horizen’s approach to mining centralization—whether it’s ASICs, pools, or marketplaces—is to explore innovative blockDAG technologies that can collapse mining difficulty and, ideally, make solo GPU mining profitable again, attracting more miners and adding more decentralization to the network.
According to Cornell professor Emin Gün Sirer, “Mining marketplaces can easily be abused, as the people who offer their hashing services often lack the ability to tell if their hashing power is being used responsibly or to launch attacks. It is very difficult, sometimes technically impossible, for the participants to know if their hashing power is being used for censorship or selfish mining or 51% attacks.”
Clearly, mining marketplaces make 51% attacks more likely, so the first defense is for marketplace operators to structure things responsibly; for instance, don’t allow a majority of hashrate to point to any one network, cut it off once it passes some threshold. Longer term, consensus rules are needed to end this threat vector. However, if things don’t change, Gün Sirer expects to see more of these kinds of attacks.
It’s not an easy challenge to stop mining marketplaces as they help to remove the knowledge gap for beginners to actually start mining like building your own mining rig and completing all the configuration and tweaking. Marketplaces like NiceHash help you to start mining in less than 30 minutes. In addition, people don’t have to worry about long-term risks like failing hardware, electricity costs, or strong price fluctuations.
Some networks like Robert’s Horizen platform try to protect themselves from 51% attacks by innovating the longest chain rule within their consensus protocol. They’re upgrading their protocol to make these kinds of attacks unfeasibly costly by introducing a delayed block penalty. Basically, 51% attacks happen by nefarious miners solving a sequence of blocks in parallel privately, then injecting them all at once to the network. Horizen penalizes such delayed block reporting, making it virtually impossible to pull off the same type of attack.
It’s clear that mining marketplaces which rent out hashing power can harm smaller cryptocurrency projects. It’s certainly not an easy task to protect us from such attacks. On the one hand, we can start improving our Proof of Work consensus algorithms to make them more resistant to 51% attacks, on the other hand, we can start working together with mining marketplaces to provide them with technology that can detect where their mining power is going, set thresholds for each crypto, and alert the marketplace owners when the hashing power is being abused.
Sources
StackExchange Bitcoin - Legal discussion on 51% attacks
TLDR; A 51% attack refers to a double-spend attack on a blockchain where an entity or group of persons controls more than 50% of the network’s mining hashrate. This gives the attackers massive control over the network and the transactions happening on it. It basically means they can manipulate transactions, revert them, or change the destination, enabling them to spend them twice.
ZenCash is not the only victim of recent a 51% attack - MonaCoin, Bitcoin Gold, Verge, and Litecoin have been attacked as well recently. It’s clear that the cost of a 51% attack isn’t that high for many smaller - and less popular among miners - Proof of Work (PoW) coins. This article discusses the following topics:
- Costs of a 51% attack
- Legal aspects of a 51% attack
- Risks of mining as a service
Costs of a 51% attack
Crypto51.app is a website that wants to bring awareness among smaller cryptocurrencies to show them how easy it is to complete a 51% attack on their network. The cost is calculated using NiceHash prices, a website that offers hashrate (mining) power on various cryptocurrencies as a service. The price is based on matching the hashrate of a specific Proof of Work network for one hour. The price does not include the block rewards the attacker may receive, according to Crypto51.app, “this can be quite significant, and reduce the attack cost by up to 80%.”
Shockingly, several smaller cryptocurrencies have plenty of hashrate for sale on NiceHash, making themselves vulnerable for a 51% attack. In the introduction we mentioned MonaCoin; Crypto51 shows us that they have almost 5 times the amount of hashing power needed to perform a 51% attack for sale via NiceHash. Here’s an extract of the list, mind Bitcoin Private and Bytecoin.

Robert Viglione, co-founder of Horizen, puts Crypto51.app into perspective, ”Proof of Work is the most battle-tested consensus mechanism and so it’s something we shouldn’t abandon lightly. Hijacking networks is now too easy, though still much more difficult than sites like crypto51.app present.”
“One still needs to buy a large amount of the target coin—these funds are at risk as the attacker is performing actions that directly undermine its value—and then gamble real money on stochastic outcomes. It involves good timing, luck, and nontrivial resources to pull off.”
A 51% attack involves good timing, luck, and nontrivial resources to pull off - Robert Viglione.
Legal aspects of a 51% attack
Would performing a successful double spend be considered illegal?
It’s a tough discussion about whether a successful double-spend is considered illegal. On the one hand, you are stealing money as people won’t receive the funds they should have received. On the other hand, there’s not really a law that recognizes international alternative currencies. Bitcoin and most other cryptocurrencies have no terms and conditions that promise to give you something in return for the currency, and no central authority to form an agreement with.
According to Chris on StackExchange, “A double-spend would be blackletter law illegal as fraud and theft include a wide variety of intentional deception wrongfully depriving someone of property - use of a government-minted currency is not, and never was a required element. Look at any larceny or fraud statute - it will refer to loss of or damage to a person and property, not monetary dollars."
If you are in the US, the law is very broad. The Computer Fraud and Abuse Act (18 U.S.C 1030) protects companies and persons against any digital attack or theft, and so, can be applied to almost any digital crime.
Should new projects use other mining algorithms as they put themselves at risk using PoW?
PoW is challenging for a new project that doesn’t start immediately with strong mining support. However, what’s also true is that the economic incentives to attack small networks just aren’t there. Why risk real funds for no reward? This is why small networks rarely get attacked. Proof of Stake (PoS) and other consensus variants have also proven to be promising thus far, so new projects ought to consider them, but there are always tradeoffs.
Risks of renting mining power
For sure, these marketplaces which rent mining power as a service add a centralizing element to what were intended to be more decentralized mining environments. Robert Viglione thinks we just need to be more creative on the entrepreneurial side to continue decentralizing when and where it makes sense.
Horizen’s approach to mining centralization—whether it’s ASICs, pools, or marketplaces—is to explore innovative blockDAG technologies that can collapse mining difficulty and, ideally, make solo GPU mining profitable again, attracting more miners and adding more decentralization to the network.
According to Cornell professor Emin Gün Sirer, “Mining marketplaces can easily be abused, as the people who offer their hashing services often lack the ability to tell if their hashing power is being used responsibly or to launch attacks. It is very difficult, sometimes technically impossible, for the participants to know if their hashing power is being used for censorship or selfish mining or 51% attacks.”
Clearly, mining marketplaces make 51% attacks more likely, so the first defense is for marketplace operators to structure things responsibly; for instance, don’t allow a majority of hashrate to point to any one network, cut it off once it passes some threshold. Longer term, consensus rules are needed to end this threat vector. However, if things don’t change, Gün Sirer expects to see more of these kinds of attacks.
It’s not an easy challenge to stop mining marketplaces as they help to remove the knowledge gap for beginners to actually start mining like building your own mining rig and completing all the configuration and tweaking. Marketplaces like NiceHash help you to start mining in less than 30 minutes. In addition, people don’t have to worry about long-term risks like failing hardware, electricity costs, or strong price fluctuations.
Some networks like Robert’s Horizen platform try to protect themselves from 51% attacks by innovating the longest chain rule within their consensus protocol. They’re upgrading their protocol to make these kinds of attacks unfeasibly costly by introducing a delayed block penalty. Basically, 51% attacks happen by nefarious miners solving a sequence of blocks in parallel privately, then injecting them all at once to the network. Horizen penalizes such delayed block reporting, making it virtually impossible to pull off the same type of attack.
The bottom line
It’s clear that mining marketplaces which rent out hashing power can harm smaller cryptocurrency projects. It’s certainly not an easy task to protect us from such attacks. On the one hand, we can start improving our Proof of Work consensus algorithms to make them more resistant to 51% attacks, on the other hand, we can start working together with mining marketplaces to provide them with technology that can detect where their mining power is going, set thresholds for each crypto, and alert the marketplace owners when the hashing power is being abused.
Sources
StackExchange Bitcoin - Legal discussion on 51% attacks

