The nature of limited supply for many digital assets and other commodity-like qualities coupled with network effects and market inefficiencies helps create extreme volatility in many cases and as can be seen historically.
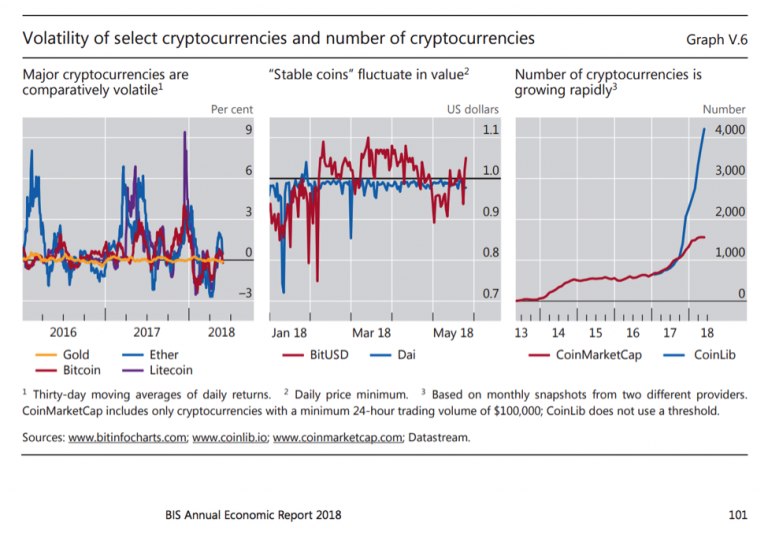
In addition to market risk, crypto-assets can be incredibly complex and have attracted countless scams, in addition to hackers who prowl for opportunities to steal users crypto-related data if not stored correctly. Below is a list of some major hacks over the years:
Source: Twitter
Cryptocurrencies, such as Bitcoin, involve the use of cryptography which is an evolving science of secret writing at the intersection of cybersecurity, math and computer science, making cryptocurrency-related products and processes some of the most complex financial products in the world.

The cryptography of bitcoin includes (but not limited to) the following cryptographic primitives:
Thousands of cryptocurrencies have come into existence in recent years thanks to cryptography technologies used in Bitcoin, such as Ethereum and other platforms where projects can be easily launched.
An entire army of scammers has flocked to these new complex products knowing that many users would be initially confused about how they work and leading to a proliferation of scams throughout the internet.
While many fraudsters might not be the smartest people, they can often employ sophisticated tactics when scamming their victims out of money.
To make matters worse, the methods and tricks used by such scam artists continually change, as they try to evade detection as the public becomes aware of how the scam operates.
Victims are usually further at a lost, as fraudsters move their geographic location elsewhere and adapt quickly in their effort to stay ahead of law enforcement or switch to a different product and change their approach, for example.
In addition, if there is an entity involved the persons associated with it could be victims too of identity theft or unaware of the fraud being perpetrated, with no way for an outsider to tell (as scammers will use proxy persons to setup shell companies).
This makes it nearly impossible for most victims to recover lost or stolen funds, and especially as cryptocurrency transactions are un-reversible and uncensorable.
Gone are the days of dealing with spam emails from Nigerian princes or others promising to wire millions in return for paying a nominal wire fee. Internet scams have gotten far more sophisticated, especially now with cryptocurrencies involved.
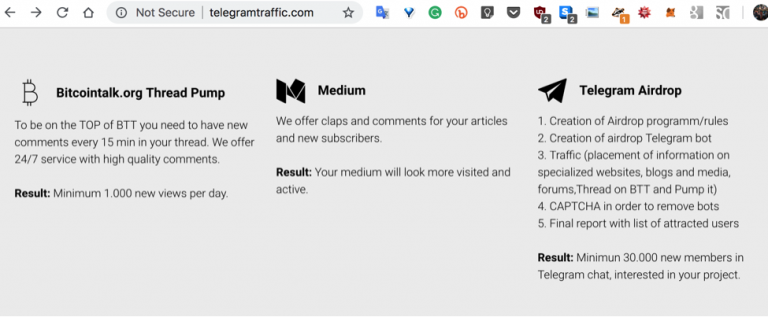
To make matters worse, there are plenty of fake volumes and fake users in groups, due to the lack of ethics by supposed service providers (who are akin to scammers) such as seen on the following site excerpt:
Here are some common channels and methods that have been observed in recent years where consumers can be easily susceptible to fraud if proper precautions are not taken, involving cryptocurrencies:
If the client doesn’t realize they are on the wrong site and enter their personal information and credit card or cryptocurrency into the scam site, there is often little means to recover funds stolen in such a manner, as such fraudsters usually use fake identities and offshore hosting for the fake clone sites.
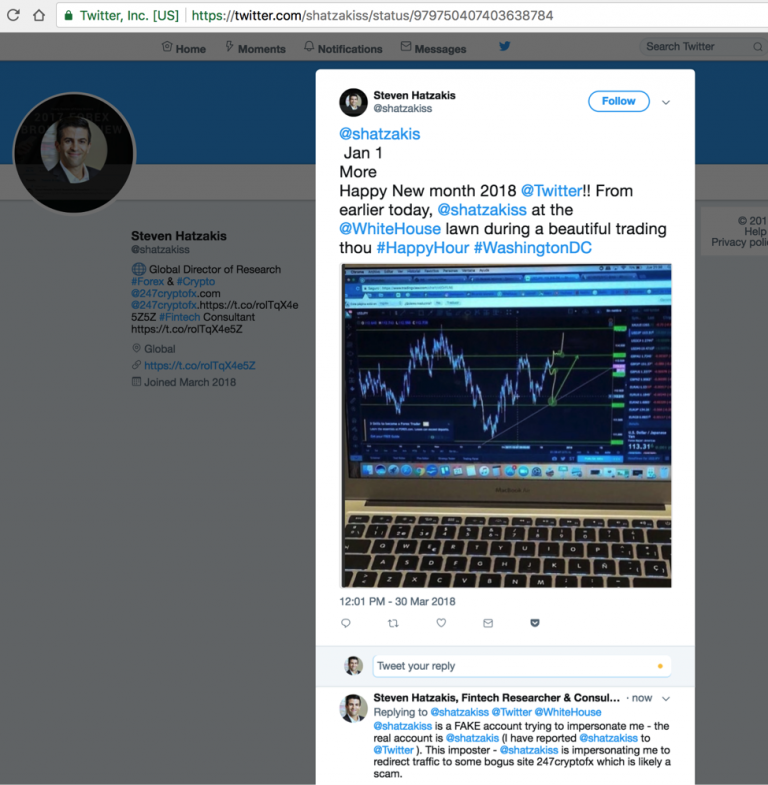
In fact, this happened once to the author of this post, where an imposter on Twitter tried impersonating his real account to trick users to visit some scam website.
At a deeper level, typosquatting even exists in programming where malicious code libraries hide in an incorrectly spelled command (with the typo) waiting for a user to accidentally run it (to execute the malicious code in an application or program).
With phishing emails, scammers hope that some consumers will first click through some call-to-action in the email, where they will be redirected to the scam website, where the attacker hopes that the user will enter their personal information or otherwise take action that the attacker will use to compromise the client financially or otherwise.
Furthermore, a scammer could even pose as a trusted friend or family member, after building a profile about their victim while attempting such social engineering tricks.
In these cases, if a consumer receives a message that appears to be from a friend or loved one, and it looks suspicious, always be sure to verify (i.e. perhaps ask a question that only the real person would know to answer).
Unfortunately, many scammers take this opportunity to try to trick users by posing as administrators or authorized representatives of the group, when in fact they are not.
This means that a fake admin will reach out to a user posing as a person of authority and make some statement requesting information for some official reason, when in fact the fake admin is just trying to steal data from the user or get the user to send cryptocurrency to some address that will cause a permanent 100% loss to the consumer that will be unrecoverable in most cases.
Users need to be especially aware when joining a group for the first time as the fake admins will sometimes reach out right away to new users. There are also bots and spammers on such platforms making it even harder for consumers.
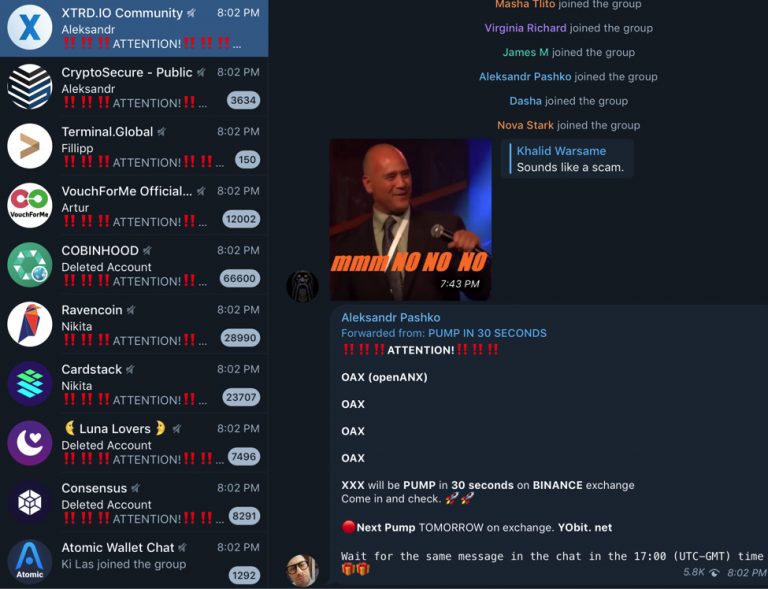
Such fake administrators have been seen on the popular messaging app Telegram, and this type of scam is like phishing and clone profiles on Twitter, as the fake administrator is often impersonating a real administrator.
Among this vast array of trusted and experimental new applications made by aspiring developers, there are also a few malicious applications trying to conceal their true intentions.
Such malicious programs wait to be installed by unsuspecting users and will either ask for certain permissions where the users data will be accessed and used by the malicious program owner to compromise the consumer.

(Photo by Icons8 team on Unsplash)
For example, one application that I read about created a meet-in-the-middle attack by using a proxy server to relay the users one-time-passcodes every time they used Two Factor Authentication (2FA) such as the Google Authenticator app to login to some service.
So even though the Google Authenticator app is secure, having a malicious app concurrently installed on the same device can compromise the security of other applications, as such passcodes should only be seen locally and not sent to another server in real-time (which is what the attackers did to steal the codes using the malicious program).
Likewise, a secure browser plugin could become insecure if there is a concurrent insecure plugin stealing the information from the site being visited where the secure plugin is being used.
Just as the action of one worker could compromise the cybersecurity for the rest of the team at an internet-based company, so can the action of a plugin compromise the security of the entire browser and its other installed plugins.
Cryptocurrency wallet software must employ cryptographically-secure pseudo-random number generators (CSPRNGs), so users can be confident that an attacker cannot recreate the state (entropy bits) that lead to their random number, and provided that all other processes remain secure (such as occurring locally).
Such a software might be thought of to be secure as all processes are created locally and the wallet is fully-functional, but if the random number generator is not cryptographically-secure, it means that an attacker could predict the next range of numbers it will output which would enable them to recreate the wallet, and thus render the wallet insecure.
It’s critically important that a user of a cryptocurrency wallet is confident that the random number generator used by the wallet is cryptographically-secure when generating a new wallet.
The above are just a few examples of categories that scams will fall into and is not meant to be exhaustive of all the types of scams and categories. For example, mining is another entire market segment of cryptocurrencies (for mineable crypto assets) where various scams exist. A scammer might combine a real product, like the sale of an Application Specific Integrated Chip (ASIC) mining hardware into their scheme in order to appear legitimate, for example.
Also, consumers can separate their device usage so that one is dedicated for secure use, and the other for experimental apps and browsing, or separate browsers for that same purpose on the same device.
Again, these are just a few points, there are many more risks, and “security is a process, not a destination”, as the famous saying goes.
I wish you a safe journey, as there are unfortunately too many scams involving buying, investing, storing and mining cryptocurrencies, which are key themes of the market, yet there are also ways to stay safe.
This article was originally published on blockchainassociation.io and is republished here with permission.

In addition to market risk, crypto-assets can be incredibly complex and have attracted countless scams, in addition to hackers who prowl for opportunities to steal users crypto-related data if not stored correctly. Below is a list of some major hacks over the years:

Source: Twitter
Product complexity attracts scammers
Cryptocurrencies, such as Bitcoin, involve the use of cryptography which is an evolving science of secret writing at the intersection of cybersecurity, math and computer science, making cryptocurrency-related products and processes some of the most complex financial products in the world.

The cryptography of bitcoin includes (but not limited to) the following cryptographic primitives:
- SHA256 (hash function to guess nonce, link blocks, and format addresses)
- Merkle Trees (storage format for blocks chained together via hashes)
- ECDSA (Diffie-Helman, public-key cryptography applied on elliptic curves)
- Elliptic Curve secp256k1 (Curve used for wallet derivation from private keys and signatures)
Thousands of cryptocurrencies have come into existence in recent years thanks to cryptography technologies used in Bitcoin, such as Ethereum and other platforms where projects can be easily launched.

An entire army of scammers has flocked to these new complex products knowing that many users would be initially confused about how they work and leading to a proliferation of scams throughout the internet.
While many fraudsters might not be the smartest people, they can often employ sophisticated tactics when scamming their victims out of money.
To make matters worse, the methods and tricks used by such scam artists continually change, as they try to evade detection as the public becomes aware of how the scam operates.
Scams today can be elusive, and hard to detect
Victims are usually further at a lost, as fraudsters move their geographic location elsewhere and adapt quickly in their effort to stay ahead of law enforcement or switch to a different product and change their approach, for example.
In addition, if there is an entity involved the persons associated with it could be victims too of identity theft or unaware of the fraud being perpetrated, with no way for an outsider to tell (as scammers will use proxy persons to setup shell companies).
This makes it nearly impossible for most victims to recover lost or stolen funds, and especially as cryptocurrency transactions are un-reversible and uncensorable.
Gone are the days of dealing with spam emails from Nigerian princes or others promising to wire millions in return for paying a nominal wire fee. Internet scams have gotten far more sophisticated, especially now with cryptocurrencies involved.
To make matters worse, there are plenty of fake volumes and fake users in groups, due to the lack of ethics by supposed service providers (who are akin to scammers) such as seen on the following site excerpt:

Common crypto scams
Here are some common channels and methods that have been observed in recent years where consumers can be easily susceptible to fraud if proper precautions are not taken, involving cryptocurrencies:
- Typosquatting: In this scheme, a fraudster examines spelling variations of known websites and chooses an available domain name that is the most common typo, and then tries to mimic the real site by posing as a fake clone.
When a user makes the predicted typo when entering the domain name incorrectly and lands on the fake site, the fraudster hopes the client will think it is the real site and proceed as usual.
If the client doesn’t realize they are on the wrong site and enter their personal information and credit card or cryptocurrency into the scam site, there is often little means to recover funds stolen in such a manner, as such fraudsters usually use fake identities and offshore hosting for the fake clone sites.
- Note: typosquatting is not limited to the domain name, this attack is also prevalent on social media sites such as Twitter where imposters use fake profiles with nearly-identical spelling variations of a real user’s profile they impersonate to trick users.
In fact, this happened once to the author of this post, where an imposter on Twitter tried impersonating his real account to trick users to visit some scam website.

At a deeper level, typosquatting even exists in programming where malicious code libraries hide in an incorrectly spelled command (with the typo) waiting for a user to accidentally run it (to execute the malicious code in an application or program).
- Phishing: Spotting a fake email is increasingly difficult. Given the number of emails people receive on average and the ability for hackers to spoof domain address (such as via domain fronting) and make it appear they are sending on behalf of a trusted address, consumers are in a tough position to detect sophisticated email phishing scams.
With phishing emails, scammers hope that some consumers will first click through some call-to-action in the email, where they will be redirected to the scam website, where the attacker hopes that the user will enter their personal information or otherwise take action that the attacker will use to compromise the client financially or otherwise.
Social Engineering
Furthermore, a scammer could even pose as a trusted friend or family member, after building a profile about their victim while attempting such social engineering tricks.
In these cases, if a consumer receives a message that appears to be from a friend or loved one, and it looks suspicious, always be sure to verify (i.e. perhaps ask a question that only the real person would know to answer).
- Fake administrators: With more and more social messaging apps becoming mainstream and the use of online collaborative groups, users are finding themselves immersed in multiple communities at a time and multiple groups, being able to connect with fellow users and consumers and interact in those communities, whether for investing or any common subject of interest.
Unfortunately, many scammers take this opportunity to try to trick users by posing as administrators or authorized representatives of the group, when in fact they are not.

This means that a fake admin will reach out to a user posing as a person of authority and make some statement requesting information for some official reason, when in fact the fake admin is just trying to steal data from the user or get the user to send cryptocurrency to some address that will cause a permanent 100% loss to the consumer that will be unrecoverable in most cases.
Users need to be especially aware when joining a group for the first time as the fake admins will sometimes reach out right away to new users. There are also bots and spammers on such platforms making it even harder for consumers.

Such fake administrators have been seen on the popular messaging app Telegram, and this type of scam is like phishing and clone profiles on Twitter, as the fake administrator is often impersonating a real administrator.
- Malicious programs: The app stores on Google Play and iOS contain countless applications with new ones added nearly every day and thousands of updates and new releases if we add the number of browser plugins available across popular browsers the total is likely in the millions.
Among this vast array of trusted and experimental new applications made by aspiring developers, there are also a few malicious applications trying to conceal their true intentions.
Such malicious programs wait to be installed by unsuspecting users and will either ask for certain permissions where the users data will be accessed and used by the malicious program owner to compromise the consumer.

(Photo by Icons8 team on Unsplash)
For example, one application that I read about created a meet-in-the-middle attack by using a proxy server to relay the users one-time-passcodes every time they used Two Factor Authentication (2FA) such as the Google Authenticator app to login to some service.
So even though the Google Authenticator app is secure, having a malicious app concurrently installed on the same device can compromise the security of other applications, as such passcodes should only be seen locally and not sent to another server in real-time (which is what the attackers did to steal the codes using the malicious program).
Likewise, a secure browser plugin could become insecure if there is a concurrent insecure plugin stealing the information from the site being visited where the secure plugin is being used.
Just as the action of one worker could compromise the cybersecurity for the rest of the team at an internet-based company, so can the action of a plugin compromise the security of the entire browser and its other installed plugins.
Cryptocurrency wallets
Cryptocurrency wallet software must employ cryptographically-secure pseudo-random number generators (CSPRNGs), so users can be confident that an attacker cannot recreate the state (entropy bits) that lead to their random number, and provided that all other processes remain secure (such as occurring locally).
- Random-number generators: When a cryptocurrency wallet is created by a user, the public-addresses are derived from private-keys, and both are very large numbers that are derived from the unique crypto wallet created locally on the user’s device (known as the wallet seed), using random number generators.
Such a software might be thought of to be secure as all processes are created locally and the wallet is fully-functional, but if the random number generator is not cryptographically-secure, it means that an attacker could predict the next range of numbers it will output which would enable them to recreate the wallet, and thus render the wallet insecure.
It’s critically important that a user of a cryptocurrency wallet is confident that the random number generator used by the wallet is cryptographically-secure when generating a new wallet.
Takeaway
The above are just a few examples of categories that scams will fall into and is not meant to be exhaustive of all the types of scams and categories. For example, mining is another entire market segment of cryptocurrencies (for mineable crypto assets) where various scams exist. A scammer might combine a real product, like the sale of an Application Specific Integrated Chip (ASIC) mining hardware into their scheme in order to appear legitimate, for example.

Here is a recap of points to avoid being a victim of cryptocurrency fraud:
- Consumers must always be highly suspicious of any website, app, or email, and triple-check these sources to be 100% sure they are originating from the intended source and not from a scam.
- Do not send money or cryptocurrency or give your personal information to anyone, unless you are totally sure beyond any shadow of a doubt that it is the correct source and you have checked multiple times from different angles.
- Never share or enter your private key or mnemonic recovery phrases (seed) into any applications or website, unless you absolutely trust that service and are sure beyond any doubt that you are running the legitimate version of the app or on the correct site and not a clone.
- Other steps one can take include the use of strong cryptographically-secure password generators that generate long-enough passwords with enough entropy in terms of security (i.e. 256 bits).
Also, consumers can separate their device usage so that one is dedicated for secure use, and the other for experimental apps and browsing, or separate browsers for that same purpose on the same device.
Again, these are just a few points, there are many more risks, and “security is a process, not a destination”, as the famous saying goes.
I wish you a safe journey, as there are unfortunately too many scams involving buying, investing, storing and mining cryptocurrencies, which are key themes of the market, yet there are also ways to stay safe.
This article was originally published on blockchainassociation.io and is republished here with permission.


