The function of a smart contract is simple: to hold assets in escrow into all parties have completed the requirements of said contract. Many blockchain projects make use of smart contracts. The idea is that they remove the need for either party to trust the other -- but what happens when you can't trust the underlying code of the smart contract itself?
Our recent review of the code for the WHEN smart contract revealed some suspicious, malicious, and downright scammy code. Read on for details.
Issue with WHEN ERC20 token
To view this code yourself, visit: WHEN smart contract
To put it plainly, the WHEN token contract enables the contract owner to steal anyone’s funds whether they’re on a centralized or decentralized exchange, hardware or software wallet, hot or cold storage, paper or brain wallet. It does not matter, they can move tokens from one wallet to another which means they can also steal them if they desire to.
In order to steal funds from any wallet, the contract owner has to first pass an Ethereum address to the function “authorizeContract”.
Function authorizeContract
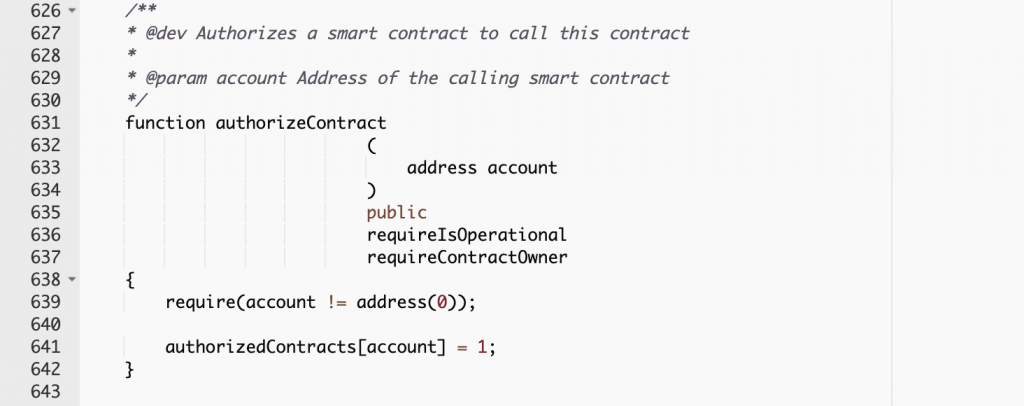
This function has a design loophole which not only allows the WHEN contract owner to enter any smart contract address of their choice but also they can pass any Ethereum wallet address here. Like shown in the above image, whenever there is a possibility of adding/editing/changing smart contracts at any time without proper measures in place, the contract owners can do anything. Because the new and undeployed smart contract can contain any kind of logic, good or evil, honest or scammy, you cannot say for sure.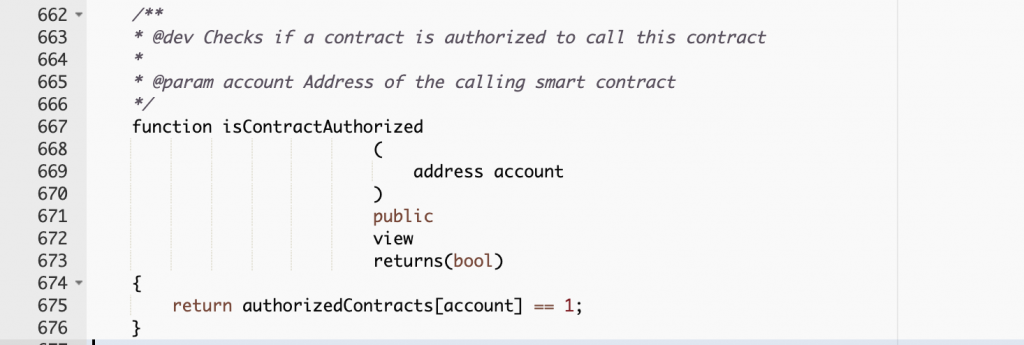
Interestingly, they only need an address they control (whether it is a smart contract or a wallet address) set into the array variable “authorizedContracts” and they are good to go. This variable is used in the function “isContractAuthorized” to check if someone has the permission to execute the next function we’ll show you below.
How WHEN Contract Owner Could Steal Your Funds?
It’s extremely easy! By calling a seemingly innocent-looking function called “vestingGrant”.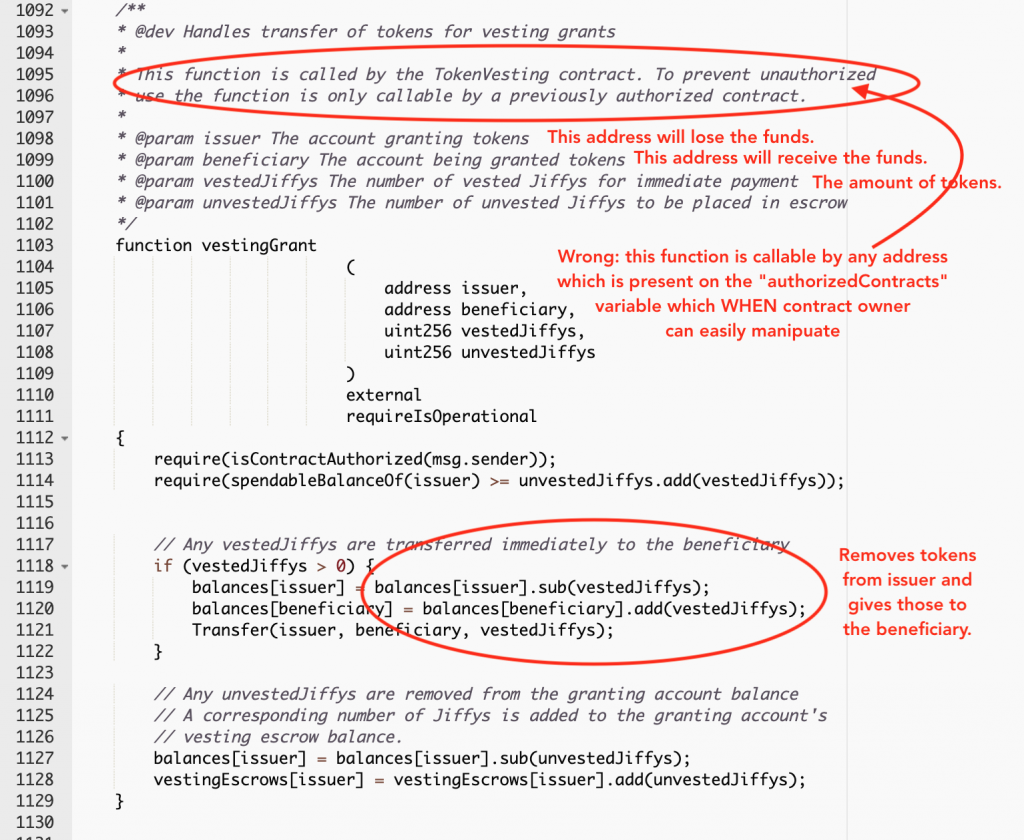
Just pass the following parameters:
- Issuer → The address from where the tokens will be stolen.
- Beneficiary → The address to where the stolen tokens will go to.
- VestedJiffys → The amount of tokens to steal.
- UnvestedJiffys or whatever that mumbo jumbo is→ 0 (zero).
Confused by what all of this means? You can learn smart contracts in plain English at Cointelligence Academy.
Exchanges failing to do their due diligence!
If that's the case then how did the WHEN token get listed on their exchange? This seems like cutting proof that IDEX doesn't do any smart contract audits or legal review before listing tokens on their exchange. So where is that $5000 going?
Looking for auditing service or due diligence service. Visit our Cointelligence Services page and learn more.
About Binod Nirvan
About Hosam Mazawi
Hosam Mazawi is the CSO of Cointelligence, the data research & analysis firm. He is an expert strategist in the cryptocurrency field. Since 2017, he has served as an advisor for several ICOs such as Alprockz and Geon Network, guiding them in their marketing and business development efforts. Hosam is also the co-founder of the LemonUnit Boutique Software House, which is offering bespoke programming.


